Unlocking The Future: How Brain Wave Authentication is Transforming Security

We are living in an age of revolutionary technological advancement, and with it comes a new wave of security measures. Brainwave authentication is becoming increasingly popular as a way to authenticate user identities and protect the data they access. Scientists have shown that each person has a unique and individual pattern of waves indicating that they might be utilized for verification purposes. currently, computerized systems are more vulnerable to hacking than ever before, making device management and security more difficult than ever. It is getting more and more challenging to maintain and regulate access while keeping user identification and system resources safe. This highlights the need to implement a strict authentication method for confirming a user’s edge devices as part of a secure infrastructure. We have come a long way from using passwords to protect our information and data, we use passwords and PINs, but brainwave authentication appears to be the most promising new security measure.
In computer security, there are three categories of authenticators
Knowledge factors (such as passwords and PINs)
Possession factors (such as physical tokens and ATM cards)
**Inherence factors (**such as fingerprints and other biometrics).
We require a way of multi-factor authentication that uses these elements but reduces the irritation caused by several steps like(entering a password followed by a distinct code from a mobile device) passthoughts aims to provide two factors of authentication in a single step to address the usability concerns associated with multi-factor authentication. A single mental activity supplies both a knowledge element (a selected hidden thought) and an inherence factor (how the concept is expressed for the individual). Passthoughts could supply an additional possession factor using a custom sensing device in a single step.

How Brain Wave Authentication Works?
Brain wave authentication technology is based on electroencephalography (EEG), which is a method of measuring electrical activity in the brain. An EEG device is placed on the head and sensors measure the brain’s electrical activity. This data is then processed using algorithms to detect patterns that are unique to each individual. The EEG device used in brain wave authentication is usually a small device that is worn on the head. It is connected to a computer or mobile device, and the data is transmitted wirelessly.
Once the EEG device is connected to the computer or mobile device, the user will be prompted to enter a password or PIN. This is done to ensure that the user is the same person as the one whose brain waves were measured. Once the user is authenticated, the EEG device will measure their brain waves and send the data to the computer or mobile device. The data is then processed using algorithms to detect patterns that are unique to each individual, after the user’s identity is verified, they are granted access to the data or information that they are trying to access.
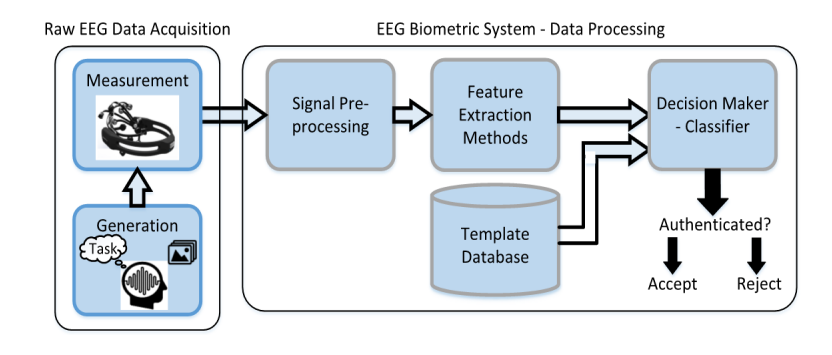
Structure of a brainwave authentication system
Generation and measurement: Executes the acquisition protocol or task that triggers unique brainwave activity and records the associated voltage fluctuations.
Signal Pre-processing: Treats the raw EEG signal to remove undesirable artifacts, such as interferences from nearby electronics, and increase the signal-to-noise ratio.
Feature Extraction: Isolates the signal components that are relevant for authentication examples are those that contain the most information about a subject.
Classification: Implements algorithms to tell authentic and non-authentic users.
Why is Brainwave Authentication more secure than other methods?
Imagine that you want to make a large purchase, such as a car or a house, using an online banking system. Traditionally, you might be required to enter a password, provide some personal information, and answer security questions to verify your identity. While these methods can be effective, they are not foolproof, as passwords can be hacked, personal information can be stolen, and security questions can be guessed or socially engineered. Brain wave authentication offers a high level of security when it comes to access control systems. These systems are based on the very individualistic patterns created by a person’s unique brain waves. By connecting people directly to specialized equipment, the system can measure and map these signals in real-time, thereby accurately determining whether the user attempting access is who they claim to be.
Some of the major security measures off EEG based systems
Unique patterns: Each individual’s brainwave patterns are unique, making it very difficult for someone to impersonate another person’s brainwaves to gain access to a system.
Difficult to spoof: Unlike other biometric authentication methods, such as facial recognition or fingerprint scans, it is extremely difficult to fool or trick a brainwave authentication system.
No physical tokens: Brainwave authentication does not require a physical token or device, which can be lost or stolen, making it less susceptible to theft or fraud.
Real-time verification: Brainwave authentication can continuously monitor a person’s brainwave patterns in real time, making it difficult for an imposter to gain access to a system undetected.
Resistance to replay attacks: Unlike other authentication methods that can be susceptible to replay attacks, where a hacker records a previous authentication attempt and replays it to gain access, brainwave authentication systems can detect this type of attack due to the unique and constantly changing nature of brainwave patterns.
Meanwhile, with the development of machine learning methods, it is now feasible to create fake brainwave data with the use of Generative Adversarial Networks (GANS). Thus, if the authentication stimuli change with each authentication attempt, the resulting brain reactions will also change, but they will still be uniquely characteristic of each user. Although the stimuli are unknown in advance, it is more difficult to create an attack using this challenge-response protocol because the attacker must be able to provide findings interactively in real-time. In Addition, an attacker who watches a person while they authenticate has no insight into their brain activity.
Users will never again need to remember passwords or carry around physical devices like ID cards because all they will need is their minds to access their accounts. Another advantage of utilizing brain wave technology is its convenience factor. The danger of data theft is considerably decreased as a further consequence of the fact that all personally identifiable information linked with the system continues to be stored in a protected location inside the servers themselves, as opposed to being stored on a single device or computer.
FINAL THOUGHTS
In conclusion, a considerable amount of work remains in the field of brainwave authentication. Even though this technology is still in its early stages of development, experts are actively working to improve its precision and dependability. To reach the optimum level of productivity, it is quite likely that a combination of different biometric technologies, such as voice recordings, facial recognition, vein scanners, and fingerprint analysis, would be utilized to verify individuals the challenge-response nature of brainwave authentication provides an added layer of security against targeted attacks and phishing, making it a promising option for applications that require strong authentication and security. Also, current advancements in machine learning algorithms are capable of enhancing the performance and accuracy of brain wave authentication systems. We may expect more security than ever before with brain wave authentication methods